WDEG - Bypassing The ASR
Introduction:
Most of us have heard about what’s called ( Windows Defender Exploit Guard ) and its components.
This article will illustrate the main idea of Windows Defender Exploit Guard and one of its components and its bypass.
What is Windows Defender Exploit Guard?
Windows Defender Exploit Guard is a software which’s being part of the Windows Defender Security Center that protects Windows OS mainly from Malware and other attacks.
WDEG Components:
- Attack Surface Reduction (ASR) – Leverages Windows Defender Anti Virus (WDAV) to disrupt commonly abused attack primitives.
- Network Protection – Blocks threats establishing outbound connection to untrusted domains / IPs.
- Controlled Folder Access – Blocks untrusted processes from accessing controlled / protected folders.
- Exploit Protection – Applies system wide mitigation settings like DEP, ASLR, CFG etc
We focused on one of the WDEG components which’s the Attack Surface Reduction ( ASR ).
As mentioned above, the ARS blocks widely used attacks:
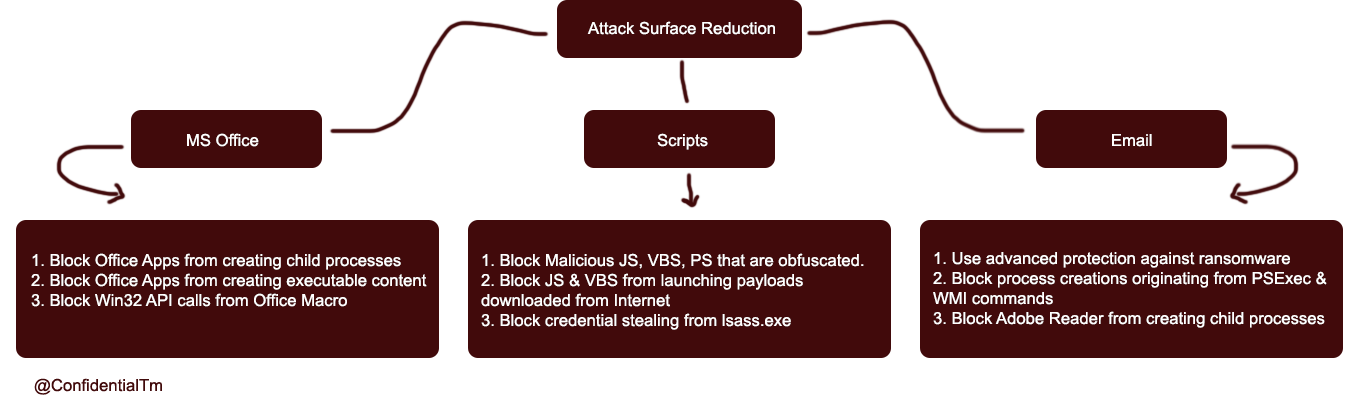
ASR uses rules mapped with GUIDs and can be enforced using PowerShell Windows Defender Package, SCCM, GPO, Local Group Policy.
- Block executable content from email client and webmail
- Block all Office applications from creating child processes
- Block Office applications from creating executable content
- Block Office applications from injecting code into other processes
- Block JavaScript or VBScript from launching downloaded executable content
- Block execution of potentially obfuscated scripts
- Block Win32 API calls from Office macro
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion
- Use advanced protection against ransomware
- Block credential stealing from the Windows local security authority subsystem (lsass.exe)
- Block process creations originating from PSExec and WMI commands
- Block untrusted and unsigned processes that run from USB
- Block Office communication application from creating child processes
- Block Adobe Reader from creating child processes
As mentioned above, the rules are being set by the GUIDs so now we can I search for each rule and its name through the Registry
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\WindowsDefender\Windows Defender Exploit Guard\ASR\Rules]
Here is each rule and its own GUDIs:
"56a863a9-875e-4185-98a7-b882c64b5ce5"="Block abuse of exploited vulnerable signed drivers"
"7674ba52-37eb-4a4f-a9a1-f0f9a1619a2c"="Block Adobe Reader from creating child processes"
"D4F940AB-401B-4EFC-AADC-AD5F3C50688A"="Block all Office applications from creating child processes"
"9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2"="Block credential stealing from the Windows local security authority subsystem (lsass.exe)"
"BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550"="Block executable content from email client and webmail"
"01443614-cd74-433a-b99e-2ecdc07bfc25"="Block executable files from running unless they meet a prevalence, age, or trusted list criterion"
"5BEB7EFE-FD9A-4556-801D-275E5FFC04CC"="Block execution of potentially obfuscated scripts"
"3B576869-A4EC-4529-8536-B80A7769E899"="Block Office applications from creating executable content"
"75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84"="Block Office applications from injecting code into other processes"
"26190899-1602-49e8-8b27-eb1d0a1ce869"="Block Office communication application from creating child processes"
"d1e49aac-8f56-4280-b9ba-993a6d77406c"="Block process creations originating from PSExec and WMI commands"
"b2b3f03d-6a65-4f7b-a9c7-1c7ef74a9ba4"="Block untrusted and unsigned processes that run from USB"
"92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B"="Block Win32 API calls from Office macros"
"D3E037E1-3EB8-44C8-A917-57927947596D"="Block JavaScript or VBScript from launching downloaded executable content"
"e6db77e5-3df2-4cf1-b95a-636979351e5b"="Block persistence through WMI event subscription"
"c1db55ab-c21a-4637-bb3f-a12568109d35"="Use advanced protection against ransomware"
Let’s take this rule:
Block JavaScript or VBScript from launching downloaded executable content
What is the meaning of this rule?
This rule prevents scripts from launching potentially malicious downloaded content. Malware written in JavaScript or VBScript often acts as a downloader to fetch and launch other malware from the Internet. (According to Microsoft)
Which means that the JavaScript and VBScript can be used by malware to run other malicious applications.
Note the ASR will not block or audit any of the execution methods unless the script executes a VBScript / JS request.
You can configure the ASR blocking rule by using the Add-MpPreference using the GUIDs and specifying the right action with this command:
-Add-MpPreference -AttackSurfaceReductionRules_Ids D3E037E1-3EB8-44C8-A917-57927947596D -AttackSurfaceReductionRules_Actions Enabled
Demo
Our team developed a tool that Bypass WDEG - ASR with some more features. Here’s a demo of that tool while executing of the requests:

PS: This technique will be illustrated with all the codes used above in one of our coming Training.
References
- https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction?view=o365-worldwide
- https://blog.palantir.com/microsoft-defender-attack-surface-reduction-recommendations-a5c7d41c3cf8
- https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/attack-surface-reduction-rules-reference?view=o365-worldwide#block-javascript-or-vbscript-from-launching-downloaded-executable-content